Privacy Protocols Landscape: Navigating the Web3 Privacy Sphere
Explore the Web3 privacy landscape with zkFi, bridging privacy and compliance in blockchain. Dive into innovations from DeFi to AI/ML & social platforms and learn how zkFi's solutions are transforming privacy.
In today's hyper-connected world, privacy is paramount. What if your bank’s financial transactions and your social account’s messages are visible to everyone, it will make you vulnerable to misuse and exploitation, right? Privacy helps limit the personal information known about us, which is crucial for safeguarding against individuals who might exploit our confidential details to disrupt our lives. The evolution of cryptography mirrors the growth of the Internet. In the early days of the web, simple encryption techniques were used to protect sensitive data, while people were less aware of privacy risks. With the rise of Web 2.0, websites and online services began to collect vast amounts of personal data, sparking privacy concerns. This led to the development of new privacy-enhancing technologies, such as encryption and ad blockers, to combat these concerns, and now we are seeing the rise of blockchain technology.
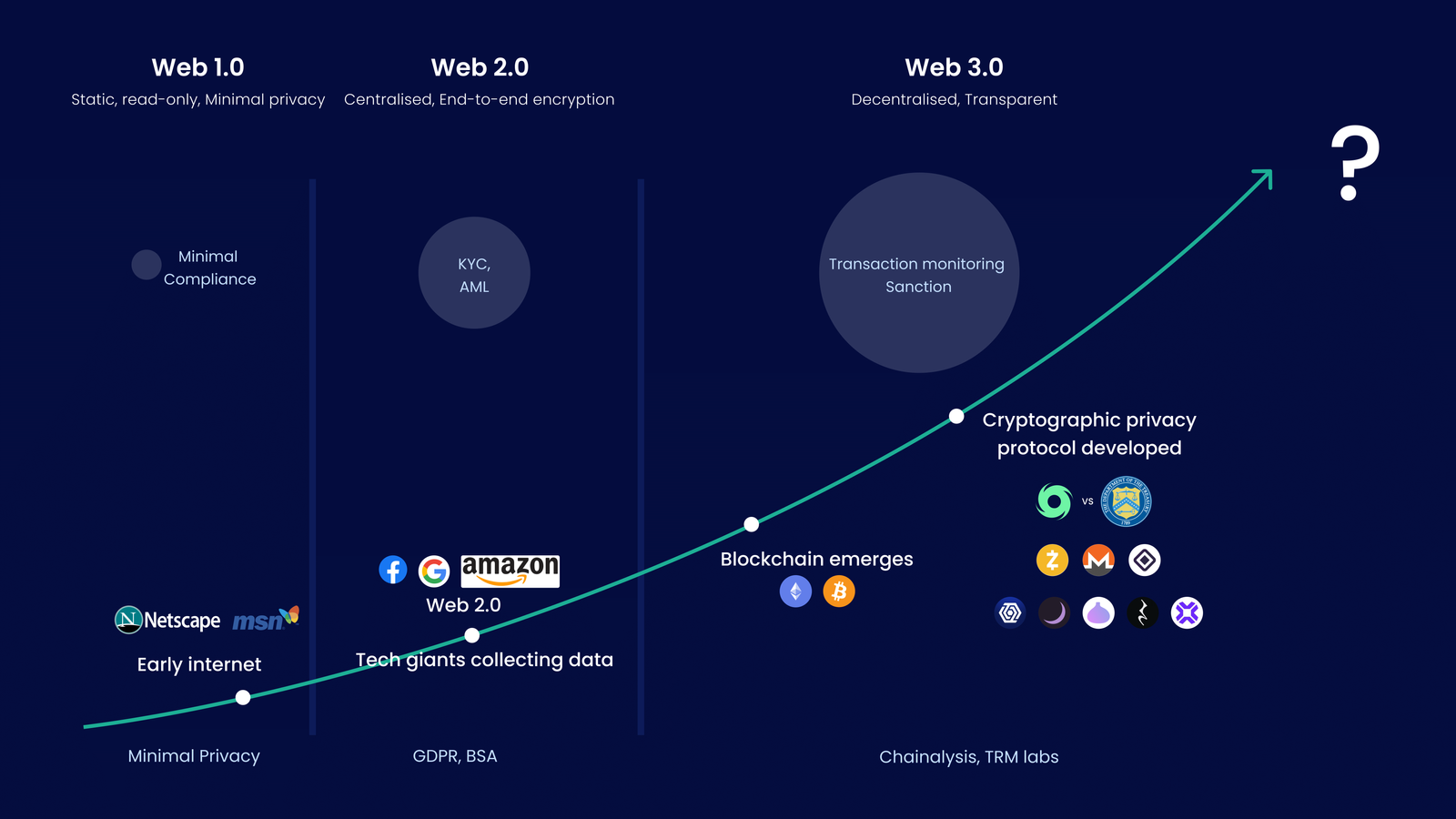
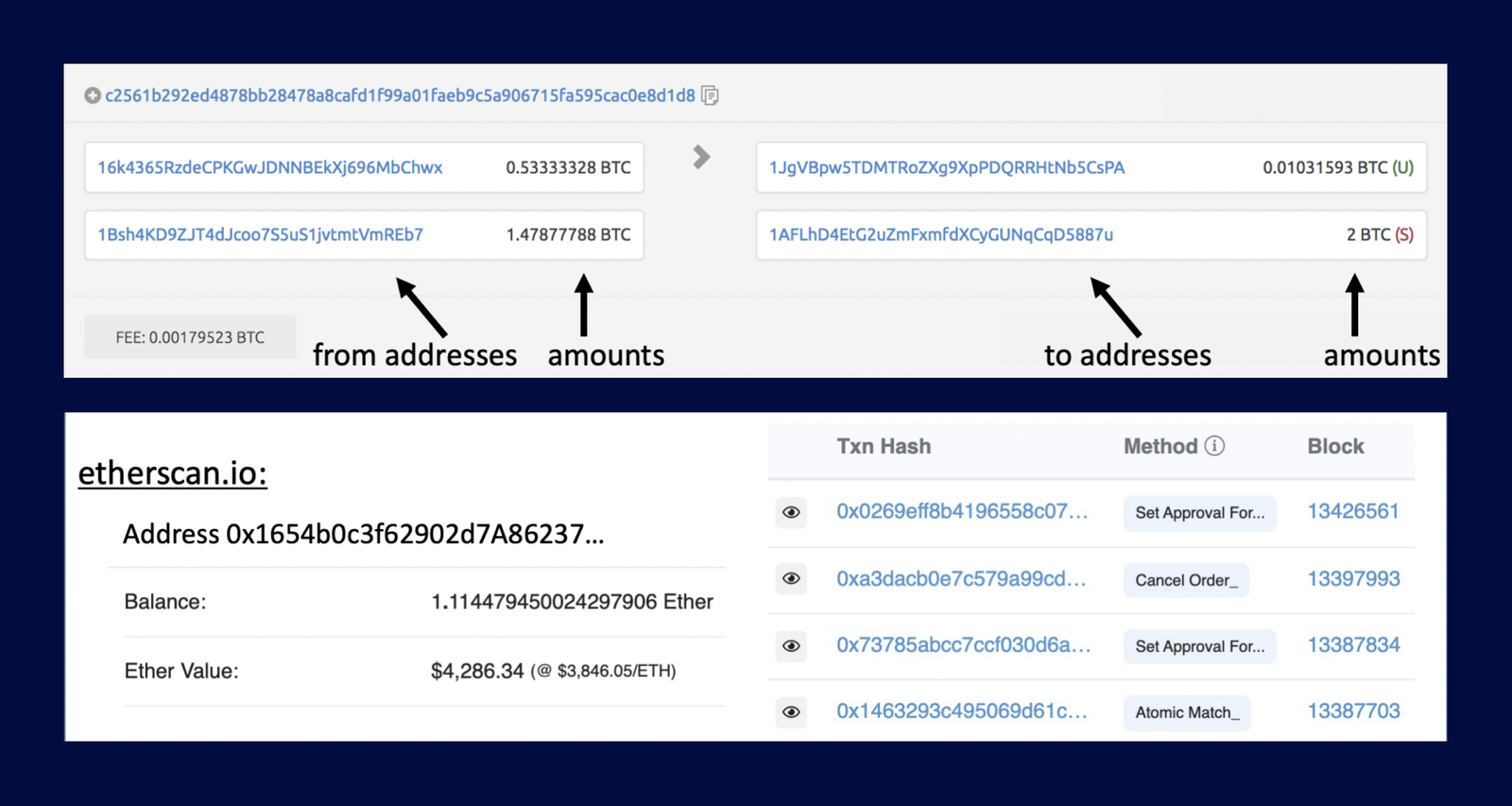
While blockchain's decentralization, immutability, and transparency are strengths that can transform industries, its transparency poses a challenge – user transactions and metadata become public once on-chain. Popular blockchains like Bitcoin and Ethereum have this challenge. It compromises user privacy, making it vulnerable to malicious actors. Transparency allows anyone with an internet connection to see any wallet holder's full transaction history, net holdings, and user's other on-chain interactions.
Individuals, businesses, and institutions hesitate to expose their financial transactions and personal data to the world. This lack of privacy is a roadblock to the mainstream adoption of Web3.
As concerns about data collection and privacy intensified, the development of privacy-enhancing technologies like zero-knowledge proofs also grew. Many innovative privacy solutions are emerging, but more work is still needed. We need efficient, robust, and decentralized compliance mechanisms to prevent illicit activities from abusing the system. Additionally, we must make UX easier and more pleasant for broader adoption. Finally, we must ensure these solutions can handle various use cases that have emerged for general-purpose use. Let's explore the privacy landscape and how zkFi provides a more substantial solution in this article.
Expanding Horizons of Private Transactions: From Asset to Data
- Emergence from DeFi to AI/ML:On one hand, while the DeFi space is growing with its various use cases for financial applications we are seeing other innovations as well using blockchain which is covered by current privacy solutions to make transaction value private there is also the emergence of an intersection between AI and crypto with new protocols like Ritual, Bittensor, Gensyn to do LLM computation in a decentralized way to solve a key concern of centralized data and security implications of LLMs as they handle vast amounts of sensitive data. These protocols enable smart contract functionality which gives new use cases in DeFi. AI agents could use crypto for payments and accessing resources. While these protocols will solve the problem with decentralized computation, the privacy problem will be unsolved.
- A New Era for Social Platforms:There are social networks like Lens, and Farcaster that address the limitations of traditional social media about centralized databases by enabling a user-owned, open social graph that allows for data portability across different applications. While these social protocols empower users and creators by giving them control over their content, reducing dependence on centralized platforms' algorithms and policies users will have to compromise privacy when they do activities like P2P messaging or do transactions on the protocol’s native payment system. Transactions may include details such as social relationships, purchasing habits, and media usage, all of which could be detrimentally misused by harmful entities. The problem becomes especially significant when user addresses are linked to actual identities via KYC.
Past And Present of Privacy Protocols Design Space
Despite many efforts on privacy-enabling projects relying on ZK, no existing solution offers a comprehensive package. These solutions struggle with either the need for robust compliance solutions, liquidity fragmentation, lack of compatibility with protocols or a cumbersome fragmented user experience. In the first innovation cycle of privacy solutions privacy-focused blockchains like ZCash and Monero pioneered anonymous transactions and also found quick adoption but they limited scope to peer-to-peer interactions, missing broader applications like DeFi.Tornado faced compliance challenges, while others like Aztec had practical issues like required asset bridging and limited interoperability. Aztec introduced a novel solution with their Layer 2 roll-up approach, which had some compatibility with DeFi. Aztec used a ZK-proof solution called Plonk to reduce costs and increase speed on Ethereum. However, it required users to bridge their assets back and forth between different chains and involved significant waiting times. This made it impractical for various DeFi interactions, such as swaps, due to the risk of slippage. Other projects face similar challenges, including weak compliance guarantees and friction in user experiences. Right now users are not confident using these protocols or feel safe to use them. Protocols have to earn trust that their assets won't be suddenly blocked or that they won't end up on a sanctions list out of the blue. This kind of trust comes from the system's leaders actively working with regulators, being open about how things work, and making it clear who is in charge. This way, users feel more secure and confident in their interactions with the privacy protocol.
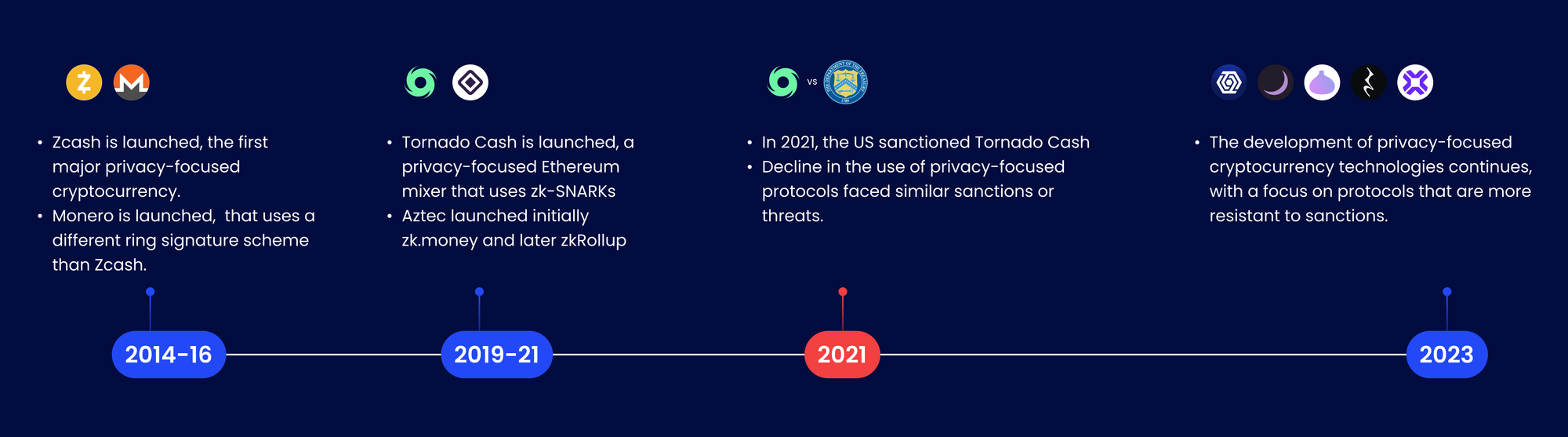
Why stand-alone privacy does not work? Learnings from Tornado Cash
Tornado Cash, a mixer protocol on Ethereum using zero-knowledge tools, provided anonymity by allowing users to deposit a fixed amount into a pool and later withdraw it without revealing their identity, breaking the link between the deposit and withdrawal. However, it became a hub for illegal funds, with criminals exploiting its privacy features. In 2022 the United States Office of Foreign Assets Control (OFAC) sanctioned Tornado Cash, accusing it of being involved in money laundering activities, including $7 billion in illegal funds and specific cases like the Ronin Bridge hack by North Korean hackers, laundering money from the Lazarus Group.
The U.S. government struggled to regulate it due to its anonymity and lack of a clear compliance strategy. This action against Tornado Cash highlighted the critical need for balancing privacy with regulatory compliance in financial protocols.

Comparison of Emerging Privacy Solutions
To understand the current state of privacy protocols, we must trace their origins. Early endeavors led to the development of cutting-edge cryptographic techniques that underpin the privacy protocols we use today. These protocols have come a long way from their nascent stages, evolving into the powerful privacy-preserving tools we now have.
Various privacy protocols have emerged in the rapidly evolving landscape of blockchain technology, each with its unique set of advantages and challenges. This section will compare four notable privacy protocols: Nocturne, Elusive, Hinkal, and Silent. We will delve into the strengths and weaknesses of each solution, including their compliance measures and potential risks.
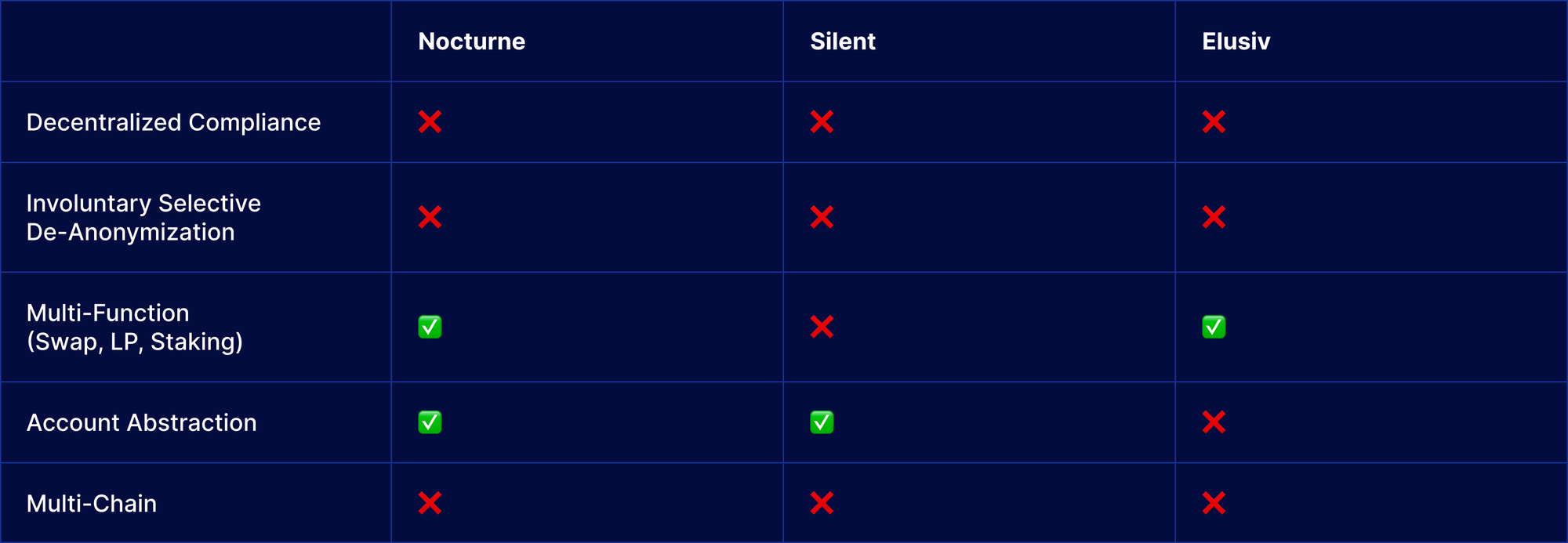
If we summarise past and present solutions we can conclude that we have great evolution in privacy space but they still lack either weak compliance or they are not covering use cases like they do not adequately address data privacy. zkFi introduces private interaction with on-chain AI and empowers users with proof of data ownership, securing sensitive information and the same is true for the on-chain social networks. Next, we will describe the various compliance methods we've noticed being used in privacy protocols.
Missing piece of compliance in the privacy landscape
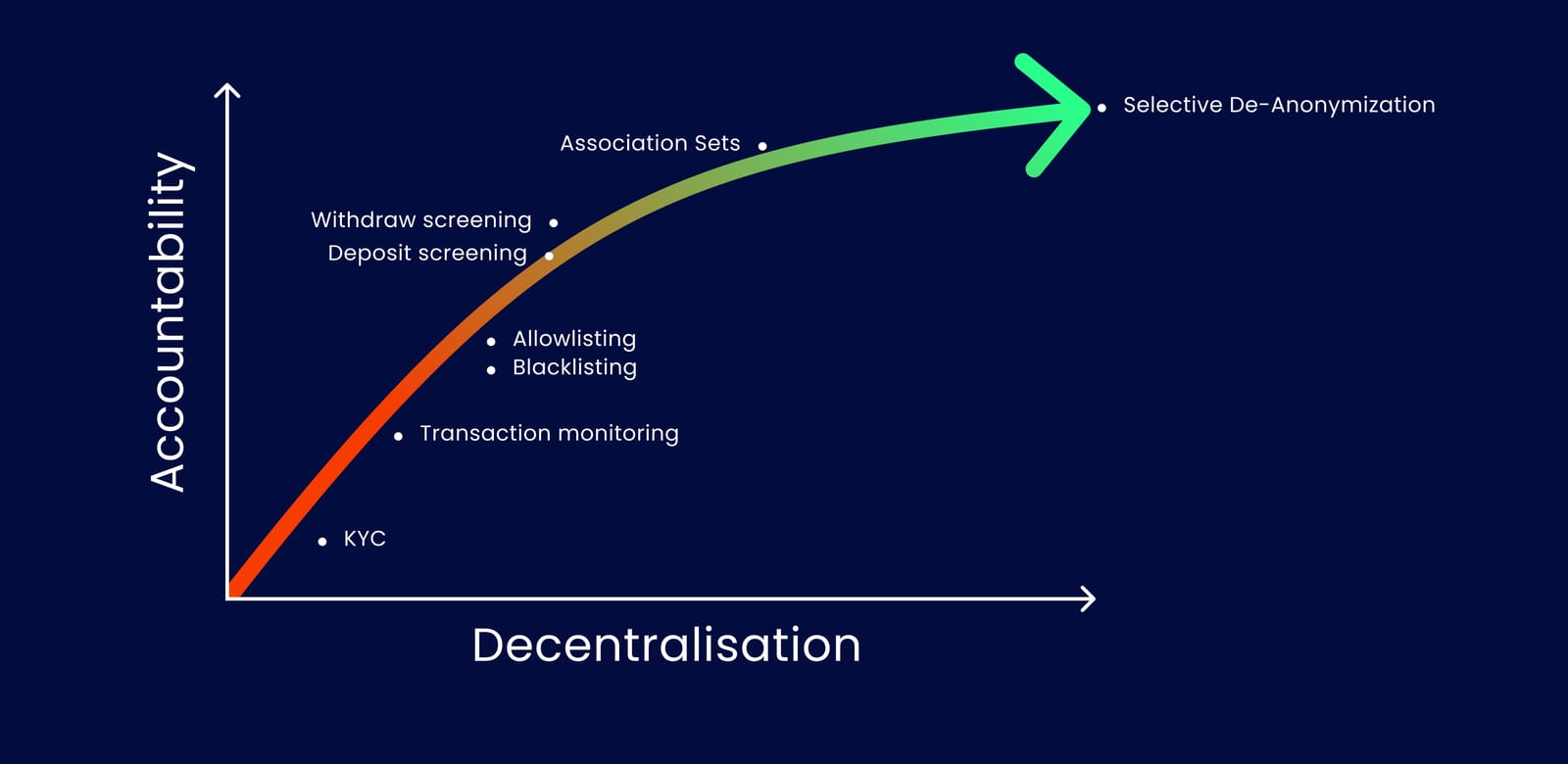
Till now, some protocols have adopted simple compliance measures to prevent illicit activity in privacy-preserving applications. For example, Protocols like Aztec's zk. money and Tornado Nova imposed deposit limits to prevent the influx of potentially illicitly obtained assets. Some protocols have blocked addresses associated with government-sanctioned entities to comply with regulatory requirements.
However, these measures often fail to provide robust compliance and protect user privacy. Malicious actors can exploit the private nature of these applications, and compliance remains a challenge. These limitations underline the need for more comprehensive and user-friendly privacy solutions in blockchain. Below, we outline the different compliance measures that we have seen employed in privacy protocols.
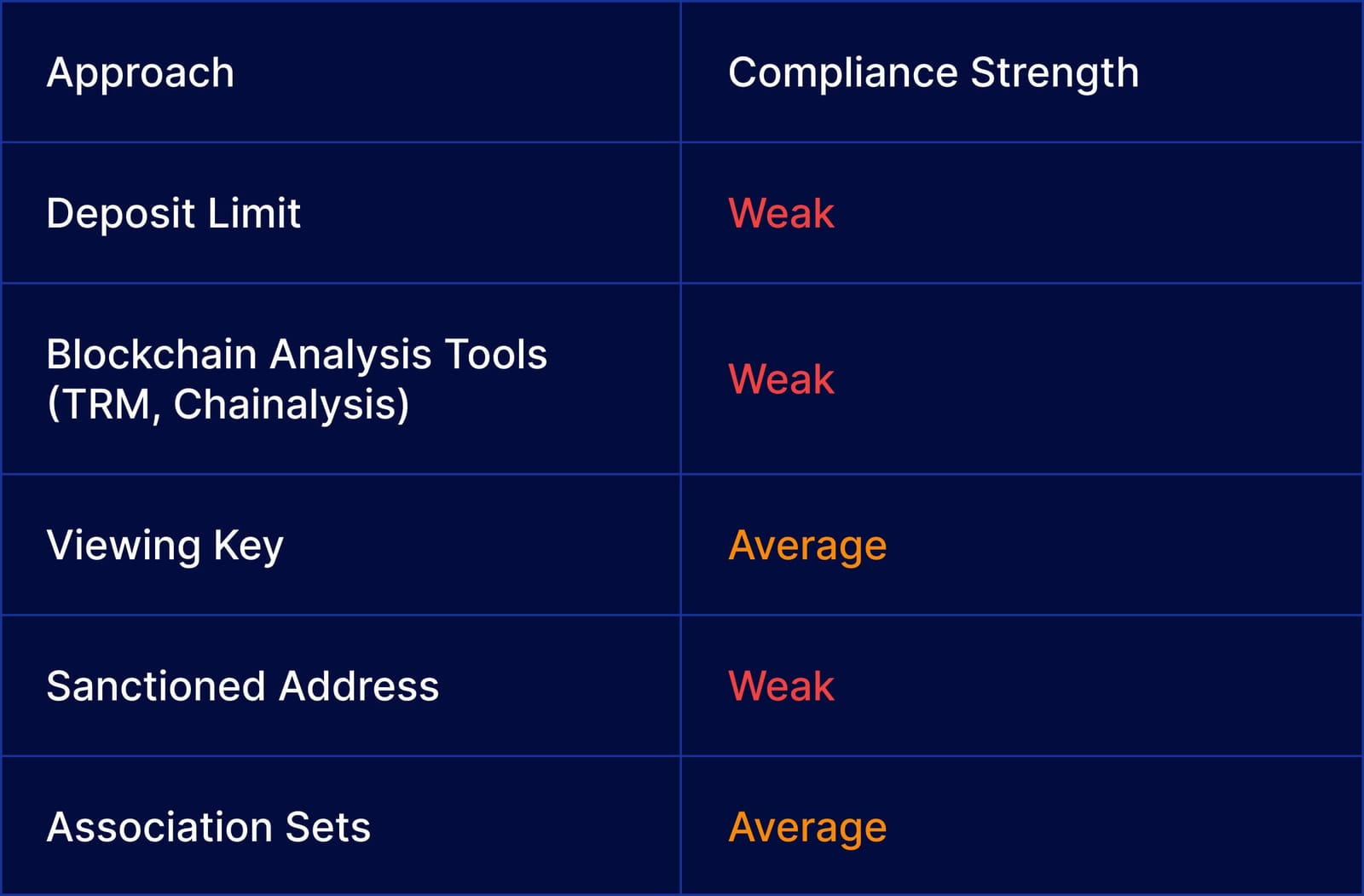
Here are some previously attempted compliance solutions, each with its limitations:
- Imposing Deposit Limit: Many applications implement deposit limits to restrict the inflow of illicitly obtained assets. While this measure can deter some malicious actors, it inconveniences legitimate users when the imposed limit is overly restrictive. This limitation confines the application's scope to small peer-to-peer payments, excluding broader use cases.
- Sanctioned Addresses: Regulatory bodies like the Office of Foreign Assets Control (OFAC) maintain lists of sanctioned entities linked to illicit transactions. Some blockchain analysis firms provide oracles to access these lists in smart contracts. While this helps identify potentially malicious actors, it has shortcomings. Malicious actors can deposit stolen funds before the list updates or send stolen assets to new addresses to evade detection. Additionally, the absence of recovery mechanisms for mistakenly listed addresses poses challenges.
- Blockchain Analysis Tools: Firms like Chainalysis and TRM Labs offer tools for tracking transactions involving illicit funds. While these tools have successfully tracked some transactions, they are inaccurate. False negatives in classification metrics can lead to untracked illicit activity, undermining the effectiveness of analysis tools.
- View-Only Access: Some privacy-preserving applications propose a view-only access mechanism through a separate view key that can decrypt transaction data without spending it. Users can share this key with authorities for regulatory purposes. However, this approach relies on voluntary user cooperation and lacks enforcement for non-cooperative or malicious users.
- A more recent solution involves using association sets by Ameen Soleimani, the originator of the privacy pool protocol, and Vitalik with other authors in privacy pools. Users can associate with a subset of deemed "good" deposits, limiting their anonymity relative to the size of this subset. This approach can assist analysis tools in linking transactions but may also result in legitimate users being associated with illicit transactions if detection occurs after a delay.The above compliance measures have partially solved the privacy protection and regulatory compliance dilemma.
zkFi: Bridging the Privacy-Compliance Gap in a decentralized design
Privacy space has struggled with the complex challenge of "Privacy trilemma" for some time now. This trilemma needs a delicate balance between three critical aspects: privacy, compliance, and decentralization. Historically, achieving all three simultaneously has proven to be a formidable task. While numerous efforts have been to enhance blockchain privacy, existing solutions often come with limitations. With zkFi we have tried to balance all three with our solution.
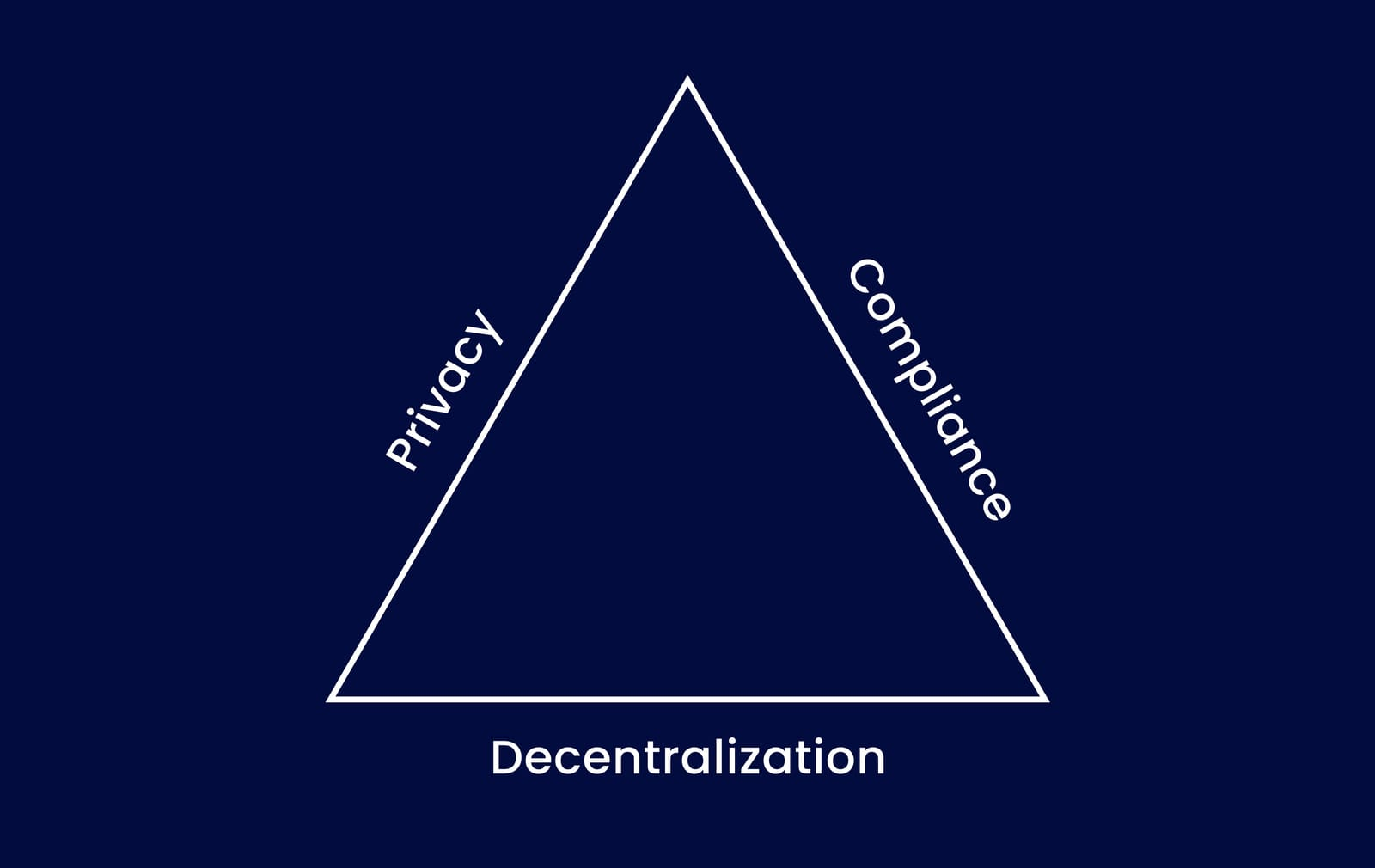
zkFi addresses the critical need to harmonize privacy and compliance in a decentralized way to solve the privacy trilemma problem. It goes beyond offering mere privacy; it delivers privacy with compliance, laying the foundation for a decentralized regulatory environment. zkFi is at the forefront of revolutionizing privacy solutions in the blockchain landscape by:
- Prioritizing Privacy: zkFi places privacy at the heart of its architecture. Leveraging advanced cryptographic techniques such as Zero-Knowledge Proofs (ZKPs), zkFi empowers users to conduct private transactions while safeguarding their confidentiality with easy UX. This transformative approach opens doors for secure interactions across various domains, including decentralized finance, payments, DAOs, social networks, and AI model interactions. zkFi envisions a future where privacy is not a luxury but a fundamental right in the decentralized digital realm.
- Decentralized Compliance: Compliance is deeply embedded in zkFi's DNA. We have designed Selective De-Anonymization (SeDe) to establish regulatory and compliant standards. This framework enables privacy-preserving applications to trace illicit transactions without central control, ensuring adherence to regulatory requirements. ZkFi maintains decentralization by distributing decision-making authority among multiple entities rather than relying on a single controlling entity. User can prove their ownership of data by viewing keys to selectively de-anonymize data to third parties, such as tax agencies or legal authorities. This approach is effective for law-abiding users, encouraging compliance with legal requirements. This empowers users and developers while ensuring regulatory compliance in a decentralized manner. Check more about zkFi compliance here.
3. zkFi SDK: A Decentralized Middleware Solution
Easy integration: To simplify the complex landscape of privacy and compliance, zkFi offers a comprehensive decentralized middleware solution.zkFi's modular design simplifies the integration of privacy and compliance features into on-chain applications. Developers can create secure, private, and compliant dApps without diving into the complexities of Zero-Knowledge Proofs (ZKPs) and compliance requirements. read more about SDK here
Private Payments via Stealth Address: zkFi provides the option of receiving assets via a stealth address, enhancing privacy by allowing users to share unique, random-looking addresses for each payment. This ensures anonymity and privacy, akin to sharing payment links with added anonymity benefits.
Shielded Wallets for Protocol UIs: zkFi integrates directly into crypto wallets, starting with MetaMask Snaps integration. Protocols can request users to spend their private assets instead of public assets from a regular wallet. This empowers protocols to design custom user interfaces while maintaining user privacy.
Multi-Chain: zkFi's multi-chain support ensures flexibility and compatibility with various blockchain ecosystems. It serves as a fundamental infrastructure for all on-chain transactions, whether human-to-human or machine-to-machine.

Enabling compliant privacy for all by catering to a wide range of use cases
- Private DeFiImagine the impact of zkFi SDK on popular DeFi protocols such as Aave, Uniswap, and Lido Finance. These protocols can leverage zkFi's capabilities to enhance their user experience significantly to provide natural interaction of privacy without leaving protocol. Here's how:Aave: zkFi can empower Aave users to transact with privacy, safeguarding their financial data while participating in lending and borrowing activities on the platform.Uniswap: By integrating zkFi SDK, Uniswap can allow privacy toggle on swapping to users to enjoy privacy without exposing their transaction details to the public, improving the overall trading experience.Lido Finance: Lido Finance can offer its users the option to engage in privacy-preserving staking activities, attracting users who value confidentiality in their financial transactions.UserWallets: A wallet backend integration of zkFi would also allow natural interaction with DeFi protocols. Wallets like Metamask, Coinbase, Rainbow, and family wallets can seamlessly incorporate privacy features into their offerings. Users of these wallets can benefit from enhanced privacy without the need to switch to a new platform or wallet.
- Data PrivacyAI/ML: Private AI/ML Interactions: zkFi ensures that users can interact with on-chain AI/ML models privately, securing sensitive inputs and outputs.Data Ownership: zkFi provides proof of data ownership, allowing users to control and monetize their data contributions to AI/ML models.Social Platforms: Full Control Over Data: Users on on-chain social platforms powered by zkFi can decide who sees their content, ensuring privacy and mitigating unwanted interactions.Data Monetization: Users can monetize their content while maintaining a private experience, fostering trust and growth in decentralized social platforms.
Conclusion
In conclusion, Privacy, compliance, and user-friendly solutions that cover broader use cases have become the cornerstones of innovation in this ever-evolving landscape of blockchain. Stay tuned as zkFi continues to shape the future of privacy, one transaction at a time. Explore the whitepaper for technical insights and research for compliance papers. Join us in revolutionizing web3 through privacy and compliance. This is just the beginning of the zkFi journey. Testnet is on the horizon, and mainnet is coming soon. If you are a developer and institution looking to integrate zkFi into your product, check zkFi documentation or please feel free to contact us via email ([email protected]). check out Twitter (@zkfi_tech) for more updates.

